Azure Red Team Bootcamp thoughts
Recently I completed a bootcamp offered by Pentesteracademy which dives into exploring and exploiting Azure services. The course has a clear offensive focus and can be used as a great starting point if you have little to no previous experience. At the end of the course I took and passed the exam to become a Certified Az Red Team Professional (CARTP).
Certified fresh
This course is (at the moment) offered through bootcamps and does not have an on-demand course. To quote the bootcamp page:
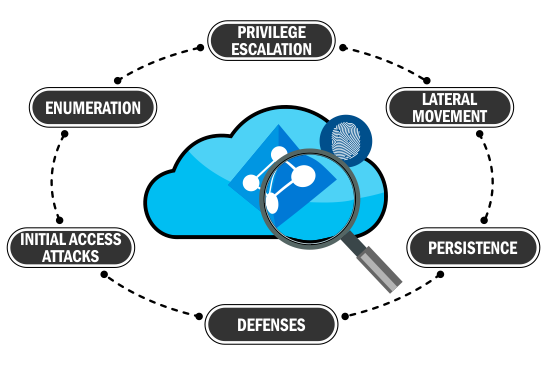
The course covers all phases of Azure Red Teaming and pentesting – Recon, Initial access, Enumeration, Privilege Escalation, Lateral Movement Persistence and Data Mining. The bootcamp will focus on methodology and techniques, through instructor demos, exercises and a hands-on lab.
There are 4 live sessions but you also get access to the video recordings and the entire course material as well and it really does what it says on the tin here. An entire cloud environment is opened up for your pleasure and you get to immediately play around with all the techniques that are shown.
Prior cloud experience is not needed in this case as the course does a good job of introducing concepts in a clear and efficient manner.
Course format
The live bootcamp format lends itself well to continous learning, between every session you have a week to go through the previous objectives step-by-step and take notes. As I took the first-ever bootcamp, the material was given out week by week but as I understand now when you join you get it all at once so you can move at your own pace too if you prefer that.
Similarly to the Certified Red Team Professional (CRTP) course, this is guided learning and you get all the answers ahead of time so you can focus on picking up the techniques without having to solve complex issues on your own.
There are pros and cons to this: The guided format can be really good to quickly boost your skills if you have no prior experience but it does not quite build the experience and familiarity that you would get if you had to progress in a lab on your own, having to research and dig into the documentation of services.
Tools of the trade
What I enjoyed most is that the bootcamp focuses on working through the same questions using multiple tools. Among others you can get familiar with:
- Azure Powershell module
- az cli
- portal.azure.com (Web GUI)
- AADInternals
- AzureHound
- Stormspotter
Each tool can excel in different scenarios and you also get examples where one particular tool can show some information but not another (due to development differences, even the Microsoft tools differ in certain regards). This is very welcome as over-reliance on any one tool can only weaken your knowledge. As you get more familiar with the concept of access tokens you will also start to pass them back and forth between tools and play with the results.
As cloud services continue to grow each of them presents an attack surface, be it function apps, web applications, automations, runbooks, virtual machines, deployment or enrollment, storage accounts and the list goes on.
The examples are sometimes simplistic but very comprehensive. As an example: One of the initial access scenario is a command execution through an Azure web app, where the code execution itself is a basic webshell upload. I was completely fine with this since the point was grabbing those access tokens quickly to move into a post-exploit scenario and seeing what you can do with it.
On the other hand by the end of the course, the last examples showcase complete tenant domination (the only thing you are not allowed to do yourself as you could literally hijack the entire lab environment forever).
Passing the exam
My only minor nitpick is about the exam itself. Even though it was a 24-hour exam the challenges were really easy and I was done in a few hours. While I would love to attribute this to my awesome preparation skills, in reality the exam so closely resembles the learning objectives that you might be able to get away with starting the exam with no prior knowledge and using the PDF as a guide. (Well I kid, but this might be a valid tip for people who have this weird certification fetish where they constantly need more letters in their Linkedin headline.)
While this means that the certificate itself won’t be a strong indicator of a person’s skill level, I do think it is not the aim of the course anyway. After passing the exam I now have a much clearer plan about what I would look for in Azure environments and how I can merge it with classic internal network techniques to pivot in and out of networks.
With remote work being what it is right now, every pentest team should put a much bigger focus on cloud environments and I can easily recommend this bootcamp as a way to get started. The price quality ratio is great as always from courses by Pentesteracademy, and just like with the CRTP back when that first launched I think the CARTP is currently filling a nice hole in offensive trainings.
Resources
If you want to learn more I highly recommend the following blogs that I’ve used, to dig deeper into some of the topics:
- https://o365blog.com/ - From the creator of AADInternals
- https://dirkjanm.io/ - For both AD and Azure related tooling and research
- https://hausec.com/azure/ - Hausec also has an interesting Azure tool called PowerZure